Chapter 14 - Enterprise Computing
This will be my final blog regarding this Computer Application class. I know i hadn't been doing a great job blogging nor have I been doing anything to improve it, but I hope what's left of my work will be enough. I am truly sorry for my lack of commitment.
Enterprise computing involves the use of computers in networks, such as LAN's and WAN's, or a series of interconnected networks that encompass a variety of different operating systems, protocols, and network architectures. Types of enterprises may include retail, manufacturing, service, wholesale, government, educational, and transportation.
Enterprise information is the information gathered in the ongoing operations of an enterptise-sized organization.
Managers coordinates resources by performing four activities. Which are, planning, organizing, leading, and controlling.
Information System in the Enterprise
A human resources information system manages one or more human resources functions. Employee relationship management systems manage communication between employees and the business.
Computer-aided design uses a computer and special software to aid in engineering, drafting, and design. Computer-aided engineering however, uses computers to text product designs. Computer-aided manufacturing is the use of computers to control production equipment. Computer-integrated manufacturing uses computers to integrate the many different operations of the manufacturing process.
Material Requirements Planning uses software to help monitor and control processes related to production. Manufacturing Resource Planning II is an extension of MRP and also includes software that helps in scheduling.
Sales force automation software equips traveling salespeople with the electronic tools they need to be more productive.
Customer interaction management software manages the day-to-day interactions with customers.
Enterprise-Wide Technologies and Methodologies
A portal is a collection of links, content, and services presented on a Web page that are interesting for a particular job function. A data warehouse is a huge database that stores and manages the data required to analyze historical and current transactions.
Web services allow business to create products and B2B interactions over the Internet.
A workflow is a defined process that identifies the specific set of steps involved in completing a particular project or business process.
A virtual private network provides mobile users, vendors, and customers with a secure connection to the company network server.
Enterprise Hardware
Enterprise hardware allows large organizations to manage and store information and data using devices geared for heavy use, maximum availability, and maximum efficiency. RAID duplicates data and implements duplication in different ways.
Network attached storage is a server that provides storage to users and information system attached to the network. A storage are network that provides storage to other servers to which it is attached. An enterprise storage system is a strategy that focuses on the availability, protection, organization, and backup of storage in a company.
A blade server packs a complete computer server on a single card rather than a system unit. A thin client is a small terminal-like computer that mostly relies on a server for data storage and processing.
High Availability, Scalability, and Interoperability
A high-availability system continues running and performing tasks for at least 99 percent of the time. May include hot-swapping and redundant components.
Scalability is a measure of how well computer hardware, software, or an information system can grow to meet increasing performance demands. Interoperability is the ability for an information with other information systems within an enterprise.
Backup Procedures
Continuous data protection provides automatic data backup whenever data is changed in an enterprise.
A disaster recovery plan is a written plan describe the steps a company would take to restore computer operations in the event of a disaster.
Thursday, 20 October 2016
Chapter 13
Chapter 13 - Computer Programs and Programming Languages
A computer program is a series of instructions that directs a computer to perform tasks. These instructions are created by a programmer using a programming language.
The machine language is the first generation of programming languages. This is the only language the computer directly recognize.
Assembly language is the second generation of programming languages. The programmer writes instructions using symbolic instruction code. A source program contains the code to be converted to machine language.
In a procedural language, the programmer writes instructions that tell the computer what to accomplish and how to do it. Such as the third-generation language
The C programming language is used to write many of today's programs.
COBOL (Common Business-Oriented Language) is designed for business applications, but easy to read because of the English-like statements.
Object-Oriented Programming Languages and Program Development Tools
An object-oriented programming language allows programmers the ability to reuse and modify existing objects. Other advantages include :
A computer program is a series of instructions that directs a computer to perform tasks. These instructions are created by a programmer using a programming language.
The machine language is the first generation of programming languages. This is the only language the computer directly recognize.
Assembly language is the second generation of programming languages. The programmer writes instructions using symbolic instruction code. A source program contains the code to be converted to machine language.
In a procedural language, the programmer writes instructions that tell the computer what to accomplish and how to do it. Such as the third-generation language
The C programming language is used to write many of today's programs.
COBOL (Common Business-Oriented Language) is designed for business applications, but easy to read because of the English-like statements.
Object-Oriented Programming Languages and Program Development Tools
An object-oriented programming language allows programmers the ability to reuse and modify existing objects. Other advantages include :
- Objects can be reused
- Programmers create applications faster
- Work well in a RAD environment
- Most program development tools are IDE's
Java is an object-oriented programming language developed by Sun Micro-systems. The Just-in-time compiler converts the byte-code into machine-dependent code.
C++ is an extension of the C programming language.
C# is based on C++ and was developed by Microsoft.
F# combines the benefits of an object-oriented language with those of a functional language.
Visual Studio is Microsoft's suite of program development tools. Visual Basic is based on the BASIC programming language. Visual C++ is based on C++. Visual C# combines the programming elements of C++ with an easier, rapid-development environment.
Power Builder is a powerful program development RAD tool. Best suited for Web-based, .NET, and large-scale enterprise object-oriented applications.
Web Page Development
Web browsers can execute short programs to add interactive elements to Web pages. To send and receive information between your computer and a web server, these programs use the CGI.
Programmers write scripts, applets, servlets, or ActiveX controls using a variety of languages.
Web 2.0 allows web sites to provide a means for users to share personal information, allows users to modify web site content, and to have a application software built into the site. Most Web 2.0 uses API's. An API enables programmers to interact with an environment such as a web site or operating system.
Web page authoring software can create sophisticated Web pages that include images, video, audio, animation, and other effects. Multimedia authoring software, however, allows programmers to combine text, graphics, animation, audio, and video in an interactive presentation.
Program Development
Program development consists of a series of steps programmers use to build computer programs.
Step 1 - Analyze Requirements : To initiate program development, programmer must first review the requirements. Next, the programmer have to meet up with the systems analyst and users. And then identify the input, processing, and output.
Step 2 - Design Solution : A solution algorithm must be designed. In structured design, the programmer typically begins with a general design and moves toward a more detailed design. Programmers often use a hierarchy chart to show program modules graphically. With object-oriented design, the programmer packages the data and the program into a single object. This is also known as encapsulation. A program flowchart graphically shows the logic in a solution algorithm.
Step 3 - Validate Design : Check for logic errors using test data.
Step 4 - Implement Design : Implementation of the design includes using a program development tool that assists the programmer by generating or providing some or all code, writing the code that translates the design into a computer program, or creating the user interface.
Step 5 - Test solution : The goal of program testing is to make sure that the programs runs accordingly and that is is error free. Errors includes syntax errors and logic errors. Debugging the program involves removing the bugs. A beta is a program that has most or all of its features and functionality implemented.
Step 6 - Document Solution : In documenting the solution, the programmer performs two activities, which is reviewing the program code, and reviewing all the documentation.
Wednesday, 19 October 2016
Chapter 12
Chapter 12 - Exploring Information System Development
What is System Development? System Development is a set of activities used to build an information system. A system is a set of components that interact to achieve a common goal. Whereas an information system is a collection of hardware, software, data, people, and procedures that work together to produce quality information. System development activities are grouped into phases, collectively called the system development life cycle.
System development follows three general guidelines, which are :
What is System Development? System Development is a set of activities used to build an information system. A system is a set of components that interact to achieve a common goal. Whereas an information system is a collection of hardware, software, data, people, and procedures that work together to produce quality information. System development activities are grouped into phases, collectively called the system development life cycle.
System development follows three general guidelines, which are :
- Group activities or tasks into phases
- Involve users
- Define standards
Project management is the process of planning, scheduling, and then controlling the activities during system development. Normally, to plan and schedule a project efficiently, the project leader should identify the project scope, the required activities, the time estimates for each activity, the cost estimates for each activity, the order of activities, and the activities that can take place at the same time.
Feasibility is a measure of how suitable the development of a system will be to the organization. Such as the operational feasibility, schedule feasibility, technical feasibility, and economic feasibility.
Documentation is the collection and summarization of data and information. For example a project notebook contains all documentation for a single project. Users and IT professionals normally refers to existing documentation when working with and modifying current systems.
Planning Phase
The planning phase for a project begins when the steering commitee receives a project request. For major activities that normally takes part in the planning phase are :
- Review and approve the project request
- Prioritize the project request
- Allocate resources
- Form a project development team
Analysis Phase
The analysis phase consists of two major activities :
-Conducting a preliminary investigation
- Determines and defines the exact nature of the problem or improvement
- Interview the user who submitted the request
-Performing detailed analysis
- Study how the current system works
- Determine the user's wants, needs, and requirements.
- Recommend a solution
Process modeling is an analysis and design technique that describes processes that transform inputs into outputs.
The project dictionary contains all the documentation and deliverables of a project. Structured English is style of writing that describes the steps in a process. Whereas data dictionary stores the data item's name, description, and other details about each data item.
Design Phase
The design phase consists of two major activities. Which are to acquire the hardware and software, as well as to develop all of the details of the new or modified information system.
A prototype is a working model of the proposed system.
-Prototypes have inadequate or missing documentation
-Users tend to embrace the prototype as a final system
-Should not eliminate or replace activities
Implementation Phase
The purpose of the implementation phase it to construct the new or modified system and then deliver it. The program development life cycle follows certain steps, which are respectively :
- Analyzing the requirements
- Designing the solution
- Validating the design
- Implementing the design
- Testing the solution
- Documenting the solution
Training involves showing users exactly how they will use the new hardware and software in the system. Such as practicing more one-on-one sessions, and implementing more classroom-style lectures as we as web-based training.
Operation, Support, and Security Phase
The purpose of the operation, support, and security phase is to provide ongoing assistance for an information system and its users after the system is implemented.
A computer security plan should carry out the these following activities :
- Identify all information assets of an organization
- Identify all security risk that may cause an information asset loss
- For each risk, identify the safeguards that exist to detect, prevent and recover from a loss
Chapter 11
Chapter 11 - Manage Computing Securely, Safely and Ethically
A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability. A cyber crime basically means an online or Internet-based illegal act. These illegal act include :
A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability. A cyber crime basically means an online or Internet-based illegal act. These illegal act include :
- Hackers
- Crackers
- Script Kiddies
- Corporate Spies
- Unethical Employees
- Cyber Terrorists
- Cyber Extortionist
Internet and Network Attacks
- A botnet is a group of compromised computers connected to a network. A compromised computer may often be known as a zombie.
- A denial of service attack (DoS attack) disrupts computer access to Internet services.
- A back door is a program or set of instructions in a program that allow users to bypass security controls.
- Spoofing is a technique intruders use to make their network or Internet transmission appear legitimate.
A firewall is a hardware or software that protects a network's resources from intrusion.
These types of hardware/software includes:
Intrusion detection software:
- Analyzes all network traffic
- Assesses system vulnerabilities
- Identifies any unauthorized intrusions
- Notifies network administrators of suspicious behavior patterns or system breaches.
Honeypot:
- Vulnerable computer that is set up to entice an intruder to break into it.
Unauthorized Access and Use
Unauthorized access is the use of a computer or network without permission. Whereas Unauthorized use is the use of a computer or its data for unapproved or possibly illegal activities.
Access controls define who can access a computer, when they can access it, and what actions that can take.
A bio-metric device authenticates a person's identity by translating a personal characteristic into a digital code that is compared with a digital code in a computer.
Digital forensics is the discovery, collection, and analysis of evidence found on computers and networks. Many areas use digital forensics, like the law enforcement, the criminal prosecutors, military intelligence, insurance agencies, and information security departments.
Software Theft
Software theft usually occurs if someone steals software media, intentionally erases programs, illegally copies a program or even illegally registers or activities a program.
A single-user license agreement typically contains certain conditions. Which is that they are permitted to install the software on one computer, make one copy of the software, or remove the software from your computer before giving it away or selling it. They are not permitted to install the software on a network, give copies to friends or colleagues while continuing to use the software, export the software, or rent or lease the software.
Information Theft
Information theft occurs only when someone steals personal or confidential information. Encryption is the process of converting readable data into unreadable characters to prevent unauthorized access.
A digital signature is an encrypted code that a person, website, or even an organization attaches to an electronic message to verify the identity of the sender. Popular security techniques includes:
- Digital certificates
- Transport Layer Security
- Secure HTTP
- VPN
System Failure
A system failure is the prolonged malfunction of a computer. A variety of factors can lead to system failure, including:
-Aging hardware
-Natural disasters
-Electrical power problems such as noise, under-voltages, and over-voltages.
-Errors in computer programs.
Two ways to protect from system failures caused by electrical power variations include surge protectors and uninterruptable power supplies.
Ethics and Society
Computer ethics are the moral guidelines that govern the use of computers and information systems. Information accuracy is a concern. Because not all information on the Web is correct.
Intellectual property rights are the rights to which creators are entitled for their work. A copyright protects any tangible form of expression.
An IT code of conduct is a written guideline that helps determine whether a specific computer action is ethical or unethical.
Green computing involves reducing the electricity and environmental waste while using a computer.
Information privacy refers to the right of individuals and companies to deny or restrict the collection and use of information about them. A cookie is a small text file that a Web server stores on your computer.
Spam is an unsolicited e-mail message or newsgroup posting. E-mail filtering blocks e-mail messages from designated sources. Anti-spam programs attempts to remove spam before it reaches your inbox.
Social engineering is defined as gaining unauthorized access or obtaining confidential information by taking advantage of trust and naivety.
Employee monitoring involves the use of computers to observe, record, and review an employee's use of a computer.
Chapter 10
Chapter 10 - Managing a Database
September 29th, 2016. Thursday.
Database - A collection of data organized in a manner that allows access, retrieval, and use of that data.
Data - A collection of unprocessed items. Such as text, numbers, images, audio, and video.
Information - Processed data. Examples: documents, audio, images, and video.
The database software, often also known as a database management system, allows users to create a computerized database, sort and retrieve data, create forms and reports from the data, as well as to add, modify, and delete data.
Valuable information normally would have numerous characteristics, such as the accuracy, verifiable, timely, accessibility, the cost-effectiveness, and many more.
The Hierarchy of Data
A character is one byte. For example, numbers, letter, space, punctuation marks, and other symbols.
A field is a combination of one or more related characters. Such as the field name, field size, and data type.
A record is a group of related fields. Normally, A primary key uniquely identifies each record. A data file is a collection of related records.
Maintaining Data
File maintenance refers to the procedures that keep data current. These procedures may refer to adding records, modifying records, or even deleting records.
Validation compares data with a set of rules or values to find out if the data is correct. Rules as such may include alphabetic or numeric check, range check, consistency check, completeness check, check gift, and other checks.
Database Management Systems
A data dictionary contains data about each file in the database and each field in those files. A DBMS provides several tools that allow users and programs to retrieve and maintain data in the database.
A query language consists of simple, English-like statements that allow users to specify the data to display, print, or store. Query by example (QBE) provides a GUI to assist user with retrieving data.
A form is a window on the screen that provides area for entering or modifying data in database. A report generator however allows users to design a report on the screen, retrieve data into the report design, and then display or print the report.
A DBMS provides means to ensure that only authorized users access data at permitted times.
Relational, Object-Oriented, and Multidimensional Databases
A data model consists of rules and standards that define how the database organizes data. A relational database on the other hard stores data in tables that consists of rows and columns. Each row normally would have a primary key whereas each column has a unique name instead. A relationship is a link within the data.
Structured Query Language is a type of query language that allows users to manage, update, and retrieve data.
An object-oriented database stores data in objects. Examples of applications appropriate for an object-oriented database include multimedia database, groupware database, computer-aided design database, and hypertext database.
A multidimensional database can store data in more than two dimensions of data. Sometimes these are also known as a hyper-cube that can consolidate data much faster than a relational database.
A data warehouse is a huge database that stores and manages the data required to analyze historical and current transactions.
Chapter 8
Chapter 8 - Types of Storage
September 22nd, 2016. Thursday.
Today in class Ms.Wan taught a new chapter. This chapter is quite an interesting chapter. Storage holds data, instructions, and information for future use. A storage medium is the physical material on which a computer keeps data, instructions, and information.
Capacity is the number of bytes a storage medium can hold. Storage are separated into Terms.These Terms may be referred in kilobytes, megabytes, gigabytes, terabytes, and many more.
A storage device is the computer hardware that records or retrieves items to and from storage media. Two functions often carried out by this storage device are reading and writing. Reading is the process of transferring items from a storage medium into memory. Whereas writing is the process of transferring items from memory to a storage medium.
The access time of a storage device is the amount of time it takes to locate an item on a storage medium. The access time may also be referred to as the time required to deliver an item from its memory to the processor.
Hard Disk
A hard disk contains one or more inflexible, circular platters that use magnetic particles to store data, instructions, and information. A hard disk could store data using longitudinal recording or perpendicular recording.
There are many characteristics of a hard disk, some includes the capacity, the platters, the revolutions per minute, the access time, and many more.
Formatting is the process of dividing the disk into tracks and sectors so that operating system can store and locate data and information on the disk.
RAID (redundant array of independent disks) is a group or two or more integrated hard disks. A network attached storage (NAS) device is a server connected to a network with the sole purpose of providing storage.
There are different types of hard disk, such as an external hard disk, which is a separate free-standing hard disk that connects to your computer with a cable or wirelessly. A removable hard disk on the other hand, is a hard disk that you insert and remove from a drive. Note that internal and external hard disk are available in miniature sizes.
Flash Memory Storage
Flash memory chips are a type of solid state media and contain no moving parts. Solid state drives (SSDs) have several advantages over hard disks, such as a faster access time, faster transfer rates, last longer, generate less heat and consumes less power.
A memory card is a removable flash memory device that could be inserted and removed from a slot in a computer, mobile device, or card reader/writer.
An Express-card module is a removable device that fits in an Express-card slot. This device is developed by thhe PCMCIA, most commonly used in notebook computers.
Cloud Storage
Cloud storage is an Internet service that provides storage to computer users.
Optical Discs
An optical disc consists or a flat, round, portable disc made of metal, plastic, and lacquer that is written and read by a laser. Typically store software, data, digital photos, movies, and music.
This laser reads on an optical disc based on 3 simple steps. Step 1, a laser diode shines a light beam toward the disc. Step 2, if light strikes a pit, it scatters. If light strikes a land, it is reflected back toward the laser diode. And for the final step, the reflected light is deflected to a light-sensing diode, which sends a digital signal of 1 to the computer. Absence of reflected light is read as a digital signal of 0.
Optical discs commonly store items in a single track that spirals from the center of the disc to the edge. The track is normally divided into evenly sized sectors.
Other Types of Storage
September 22nd, 2016. Thursday.
Today in class Ms.Wan taught a new chapter. This chapter is quite an interesting chapter. Storage holds data, instructions, and information for future use. A storage medium is the physical material on which a computer keeps data, instructions, and information.
Capacity is the number of bytes a storage medium can hold. Storage are separated into Terms.These Terms may be referred in kilobytes, megabytes, gigabytes, terabytes, and many more.
A storage device is the computer hardware that records or retrieves items to and from storage media. Two functions often carried out by this storage device are reading and writing. Reading is the process of transferring items from a storage medium into memory. Whereas writing is the process of transferring items from memory to a storage medium.
The access time of a storage device is the amount of time it takes to locate an item on a storage medium. The access time may also be referred to as the time required to deliver an item from its memory to the processor.
Hard Disk
A hard disk contains one or more inflexible, circular platters that use magnetic particles to store data, instructions, and information. A hard disk could store data using longitudinal recording or perpendicular recording.
There are many characteristics of a hard disk, some includes the capacity, the platters, the revolutions per minute, the access time, and many more.
Formatting is the process of dividing the disk into tracks and sectors so that operating system can store and locate data and information on the disk.
RAID (redundant array of independent disks) is a group or two or more integrated hard disks. A network attached storage (NAS) device is a server connected to a network with the sole purpose of providing storage.
There are different types of hard disk, such as an external hard disk, which is a separate free-standing hard disk that connects to your computer with a cable or wirelessly. A removable hard disk on the other hand, is a hard disk that you insert and remove from a drive. Note that internal and external hard disk are available in miniature sizes.
Flash Memory Storage
Flash memory chips are a type of solid state media and contain no moving parts. Solid state drives (SSDs) have several advantages over hard disks, such as a faster access time, faster transfer rates, last longer, generate less heat and consumes less power.
A memory card is a removable flash memory device that could be inserted and removed from a slot in a computer, mobile device, or card reader/writer.
An Express-card module is a removable device that fits in an Express-card slot. This device is developed by thhe PCMCIA, most commonly used in notebook computers.
Cloud Storage
Cloud storage is an Internet service that provides storage to computer users.
Optical Discs
An optical disc consists or a flat, round, portable disc made of metal, plastic, and lacquer that is written and read by a laser. Typically store software, data, digital photos, movies, and music.
This laser reads on an optical disc based on 3 simple steps. Step 1, a laser diode shines a light beam toward the disc. Step 2, if light strikes a pit, it scatters. If light strikes a land, it is reflected back toward the laser diode. And for the final step, the reflected light is deflected to a light-sensing diode, which sends a digital signal of 1 to the computer. Absence of reflected light is read as a digital signal of 0.
Optical discs commonly store items in a single track that spirals from the center of the disc to the edge. The track is normally divided into evenly sized sectors.
Other Types of Storage
- A magnetic stripe card contains a magnetic stripe that stores information. A smart card stores data on a thin microprocessor embedded in the card.
- Microfilm and microfiche store microscopic images of documents on a roll or sheet film.
- Enterprise storage stores huge volumes of data and information for large business.
Monday, 17 October 2016
Chapter 7
Chapter 7 - Understanding Output
September 20th, 2016. Tuesday.
An output is the data that has been processed into a useful form. An output device is any type of hardware component that conveys information to one or more people.
What about a display device? A display device visually conveys text, graphics, and video information. A monitor however, is packaged as a separated peripheral. These may also be referred to as a LCD monitor or a widescreen.
A liquid crystal display (LCD) uses a liquid compound to present information on a display device. The quality of an LCD monitor or LCD screen depends primarily on :
September 20th, 2016. Tuesday.
An output is the data that has been processed into a useful form. An output device is any type of hardware component that conveys information to one or more people.
What about a display device? A display device visually conveys text, graphics, and video information. A monitor however, is packaged as a separated peripheral. These may also be referred to as a LCD monitor or a widescreen.
A liquid crystal display (LCD) uses a liquid compound to present information on a display device. The quality of an LCD monitor or LCD screen depends primarily on :
- Resolution
- Response time
- Brightness
- Dot pitch
- Contrast ratio
The resolution of a display device it the number of horizontal and vertical pixels present in it. A higher resolution basically uses a greater number of pixels.
Plasma monitors are display devices that use gas plasma technology and offer screen sized up to 150 inches.
A CRT monitor is a desktop monitor that contains a cathode-ray tube. It has a much larger footprint compared to LCD monitors.
Printers
A printer produces text and graphics on a physical medium. Printed information is called a hard copy, or printout. There are two ways of printing, either in landscape or portrait orientation.
A non-impact printer forms character and graphics on a piece of paper without actually striking the paper. These types of printers includes ink-jet printers, photo printers, laser printers, thermal printers, mobile printers, and many more.
An ink-jet printer forms characters and graphics by spraying tiny drops of liquid ink onto a piece of paper. It can be printed in color or in black-and-white.
A photo printer produces color photo-lab-quality pictures. Software such as PictBridge allows you to print photos directly from a digital camera. Photo printers may also print from a memory card and preview photos on a built-in LCD screen. Most photo printer uses the ink-jet technology.
A multi-function peripheral (MFP) is a single device that prints, scans, copies, and in some cases, faxes. Sometime also known as an all-in-one device.
Impact printers form characters and graphics on a piece of paper by striking a mechanism against an inked ribbon that physically contacts the paper. Impact printers may be categorized into two types, which is the dot-matrix printer and the line printer.
A dot-matrix printer produces printed images when tiny wire pins on a print head mechanism strike an inked ribbon.
A line printer prints an entire line at a time.
Speakers, Headphones, and Earbuds
An audio output device produces music, speech, or other sounds. Most computer users attach speakers to their computers to generate higher-quality sounds for playing games, to interact with multimedia presentations, listen to music, and to watch movies.
Headphones are speakers that cover or are placed outside of the ear. Whereas earbuds, rest inside the ear canal.
Voice output occurs when you hear a person's voice or when the computer talks to you through the speakers. Some web sites dedicate themselves to providing voice output.
Other Output Devices
Other output devices are available for specific uses and applications, such as data projectors, interactive whiteboards, force-feedback game controllers, and tactile output.
A data projector is a device that takes the text and images displaying on a computer screen and projects them on a larger screen. LCD projector and digital light processing (DLP) projector are examples of data projector.
An interactive whiteboard is a touch-sensitive device, resembling a dry-erase board, that displays the image on a connected computer screen.
Sunday, 16 October 2016
Chapter 5
Chapter 5 - Types of Utility Programs and Operating Systems
September 14th, 2016. Wednesday.
System Software consists of the programs that control or maintain the operations of the computer and its device. System software are such as operating systems and utility programs.
An operating system or other words also known as (OS) is a set of programs containing instructions that work together to coordinate all the activities that work together to coordinate all the activities among computer hardware resources. These activities includes the starting and the shut down of a computer, the management of the memories and programs in the computer, task coordination, internet connection establishment, monitor performance, administer security, and so on.
Operating System Functions
The process of starting or restarting a computer is called booting. This booting may be specified into two different groups, which are cold booting and warm booting. Cold booting is when you are turning on a computer that has been powered off completely. Whereas warm booting you are using the operating system to restart the computer.
A boot drive is the drive from which your computer starts. You may also boot from a boot disk. A recovery disk contains a few system files that will start the computer.
A user interface controls how you enter data and instructions and how information is displayed on the screen. With a graphical user interface (GUI), you interact with menus and visual images.
Memory management optimizes the use of RAM. Virtual memory is a portion of a storage medium functioning as additional RAM.
A performance monitor is a program that assesses and reports information about various computer resources and devices.
Stand-Alone Operating Systems
Windows 7 provides programs such as Windows Firewall, Windows DVD Maker, WIndows Media Player, Desktop Gadget Gallery, and many more. These are examples of stand-alone operating systems.
The Macintosh operating system has set the standard for operating system ease of use. Latest version of such is the Mac OS X.
Utility Programs
A utility program is a type of system software that allows a user to perform maintenance-type tasks.
A file manager is a utility that performs functions related to file management. Such as displaying a list of files, organizing files in folders, and creating shortcuts.
A search utility is a program that attempts to locate a file on your computer based on criteria you specify.
Disk defragmenter reorganizes the files and unused space on a computer's hard dish so that the operating system accesses data more quickly and programs run faster. This process is known as defragmenting.
Spyware is a program placed on a computer without the user's knowledge that secretly collects information about the user. Note that a spyware remover could detect and delete spywares and other similar programs.
Adware displays on online advertisement is a banner or pop-up window. An adware remover is a program that detects and deletes adware.
A media player allows you to view images and animation, listen to audio , and watch video files on your computer.
Disc burning software writes text, graphics, audio, and video files on a recordable or rewritable optical disc.
A personal computer maintenance utility identifies and fixes operating system problems, detect and repairs disk problems, and includes the capability of improving a computer's performance.
September 14th, 2016. Wednesday.
System Software consists of the programs that control or maintain the operations of the computer and its device. System software are such as operating systems and utility programs.
An operating system or other words also known as (OS) is a set of programs containing instructions that work together to coordinate all the activities that work together to coordinate all the activities among computer hardware resources. These activities includes the starting and the shut down of a computer, the management of the memories and programs in the computer, task coordination, internet connection establishment, monitor performance, administer security, and so on.
Operating System Functions
The process of starting or restarting a computer is called booting. This booting may be specified into two different groups, which are cold booting and warm booting. Cold booting is when you are turning on a computer that has been powered off completely. Whereas warm booting you are using the operating system to restart the computer.
A boot drive is the drive from which your computer starts. You may also boot from a boot disk. A recovery disk contains a few system files that will start the computer.
A user interface controls how you enter data and instructions and how information is displayed on the screen. With a graphical user interface (GUI), you interact with menus and visual images.
Memory management optimizes the use of RAM. Virtual memory is a portion of a storage medium functioning as additional RAM.
A performance monitor is a program that assesses and reports information about various computer resources and devices.
Stand-Alone Operating Systems
Windows 7 provides programs such as Windows Firewall, Windows DVD Maker, WIndows Media Player, Desktop Gadget Gallery, and many more. These are examples of stand-alone operating systems.
The Macintosh operating system has set the standard for operating system ease of use. Latest version of such is the Mac OS X.
Utility Programs
A utility program is a type of system software that allows a user to perform maintenance-type tasks.
A file manager is a utility that performs functions related to file management. Such as displaying a list of files, organizing files in folders, and creating shortcuts.
A search utility is a program that attempts to locate a file on your computer based on criteria you specify.
Disk defragmenter reorganizes the files and unused space on a computer's hard dish so that the operating system accesses data more quickly and programs run faster. This process is known as defragmenting.
Spyware is a program placed on a computer without the user's knowledge that secretly collects information about the user. Note that a spyware remover could detect and delete spywares and other similar programs.
Adware displays on online advertisement is a banner or pop-up window. An adware remover is a program that detects and deletes adware.
A media player allows you to view images and animation, listen to audio , and watch video files on your computer.
Disc burning software writes text, graphics, audio, and video files on a recordable or rewritable optical disc.
A personal computer maintenance utility identifies and fixes operating system problems, detect and repairs disk problems, and includes the capability of improving a computer's performance.
Sunday, 18 September 2016
Chapter 6
Chapter 6 - Understanding Input
September 13th, 2016.
Understanding Input. What defines an input? An input basically is any data and instructions entered into the memory of a computer. Furthermore, instructions can be entered into the computer in the form of programs, commands, and user responses.An input device is any hardware component that allows users to enter data and instructions into a computer.
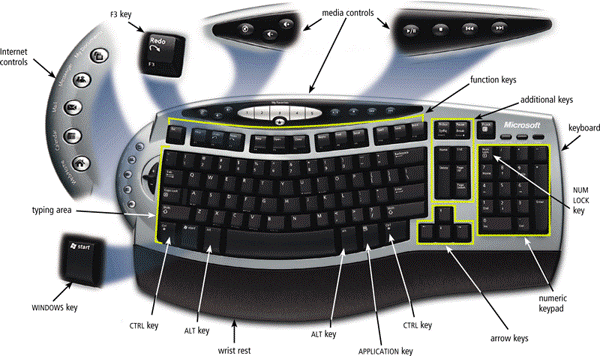
The Keyboard
A keyboard is an input device that contains keys users press to enter data and instructions into a computer.
Fun-fact, did you know that most desktop computer keyboards have between 101 and 105 keys? Most desktop keyboards also have a numeric keypad on the right side of the keyboard. It also have function keys, CTRL keys, ALT keys, and arrow keys. Besides those, WINDOWS key, APPLICATION key, and toggle can also be found on most desktop computer keyboards.
The insertion point, also known as the cursor, is a symbol on the screen that indicates where the next character you type will appear. In other words, it is also known as the mouse cursor.
Keyboards come in many variety. Generally, there are still only two types of keyboards, which are the wired keyboards (USB) and the wireless keyboards (Bluetooth/IrDA).
An ergonomic keyboard, however, has a special design which reduces the chance of wrist and hand injuries. Ergonomics incorporates comfort, efficiency, and safety into the design of the workplace.
Pointing Devices
A pointing device is an input device that allows a user to control a pointer on the screen. A pointer however is a small symbol on the screen whose location and shape change as a user moves a pointing device.Mouse
A mouse is a pointing device that fits under the palm of your hand comfortably. It can either be wired or wireless.
Other Pointing Devices
A trackball is a a stationary pointing device with a ball on its top or side. Normally used for scrolling up and down a webpage.
A touch-pad is a small, flat, rectangular pointing device that is sensitive to pressure and motion. Examples are those that are normally present on a laptop.
A pointing stick is a pressure-sensitive pointing device shaped like a pencil eraser that is positioned between key on a keyboard. Something like this:
Touch Screens and Touch-Sensitive Pads
Generally, there are two types of touch sensitive surfaces. Which are:
Microsoft Surface
Touch-sensitive pads
Pen Input
With pen input, you touch a stylus or digital pen on a flat surface to write, draw, or make selections.
Game Controllers
Video games and computer games use a game controller as the input device that directs movements and actions of on-screen objects. Such as:
- Gamepads
- Joysticks and Wheels
- Light guns
- Dance pads
- Motion-sensing controllers
Digital Cameras
A digital camera is a mobile device that allows users to take pictures and store them digitally. Studio cameras, field cameras, and point-and-shoot camera are examples of a digital camera.
There are two factors that affect the quality of digital camera photos:
Resolution
- Resolution is the number of horizontal and vertical pixels in a display device.
- A pixel is the smallest element in an electronic display.
Number of bits stored in each pixel
- Each pixel consists of one or more bits of data.
- The more bits used to represent a pixel, the more colours and shades of gray that can be represented.
Voice Input
Voice input is the process of entering input by speaking into a microphone. Voice recognition however is the computer's capability of distinguishing spoken words.
Audio input is the process of entering any sound into the computer. Sounds includes speech, music, sound effect, and many more.
Video input is the process of capturing full-motion images and storing them on a computer's storage medium.
A Web cam is a type of digital video camera that enables a user to capture video and still images, send e-mail messages with video attachments, add live images to instant messages, broadcast live images over the Internet, and to make video telephone calls.
A video conference is a meeting between two or more geographically separated people.
Scanners and Reading Devices
There are 4 types of scanners and reading devices that we learnt, which are:
- Flatbed
- Pen or Handheld
- Sheet-fed
- Drum
Optical character recognition involves reading characters from ordinary documents. A turnaround document is a document you return to the company that creates and sends it.
Optical mark recognition reads hand-drawn marks such as small circles or rectangles. An OMR device scans the documents and matches the patterns of light.
Magnetic stripe card readers read the magnetic stripe on the back of cards such as:
- Credit cards
- Entertainment cards
- Bankcards
- Other similar cards
Bio-metric Input
Bio-metrics authenticates a person's identity by verifying a personal characteristics, such as;
- Fingerprint reader
- Face recognition system
- Hand geometry system
- Voice verification system
- Signature verification system
- Iris recognition system
- Retinal scanners
Input Devices for physically Challenged Users
Several input devices are available to assists physically challenged users, such as the keyguard, keyboards with larger keys, on-screen keyboard, various pointing devices, head-mounted pointer, gesture recognition, and computerized implant devices.
Friday, 16 September 2016
Chapter 4(b)
Chapter 4(b) - System Unit Components
September 8th, 2016.
Due to my absence in blogging I would firstly wish to apologize for procrastinating this awfully. Without further ado, let's begin the second half of chapter 4, System Unit Components.
ROM
Read-only memory, or in other words also know as ROM, refers to memory chips storing permanent data and instructions. Examples may include a firmware.
s
Furthermore, A programmable read-only memory, otherwise known as PROM, is a blank ROM chip that can be written to permanently.
There are also such thing as electrically erasable programmable read-only memory, also known as EEPROM. Memories as such can be erased easily.
CMOS technology provides high speeds and consumes little power.
Access Time
Access time is the amount of time it takes the processor to read from the memory. It is also measured in nanoseconds.
Expansion Slots and Adapter Cards
An expansion slot is a socket on the motherboard that can hold an adapter card
An adapter card on the other hand enhances functions of a component of the system unit and/or provides connections to peripherals.
With Plug and Play, the computer automatically can configure adapter cards and other peripherals as you install them.
Removable flash memory may include memory cards, USB flash drives, and PC Cards/ExpressCard modules.
Ports and Connectors
A port, sometimes also referred to as a jack, is at which a peripheral attaches to or communicates with a system unit. A connector is what joins a cable to a port.
On a notebook computer, the ports are on the back, front, and/or sides.
A USB port can connect up to 127 different peripherals together with a single connector. It is also able to attach multiple peripherals using a single USB port with a USB hub.
Other types of ports also include:
- Firewire port
- Bluetooth port
- SCSI port
- eSATA port
- IrDA port
- Serial port
- MIDI port
A Bluetooth wireless port adapter converts a USB port into a Bluetooth port whereas a smart phone might communicate with a notebook computer using IrDA port.
A port replicator is an eternal device that provides connections to peripherals through ports built into the device.
A docking station is an external device that attaches to a mobile computer or device.
Buses
A bus allows the various devices both inside and attached to the system unit to communicate with each other. Examples are data bus and address bus.
Word size is the number of bits the processor can interpret and execute at a given time.
Expansion slots are connected to expansion buses. Common types of expansion buses include PCI bus, PCI Express bus, Accelerated Graphics Port, USB Firewire bus, and PC card bus.
Bays
A bay is an opening inside the system unit in which you can install additional equipment.
Power Supply
The power supply converts the wall outlet AC power into DC power.
Some external peripherals have an AC adapter, which is an external power supply.
Keeping Your Computer or Mobile Device Clean
Keeping your computer clean is essential and every computer owner just know the basics of cleaning it. Failing to do so will harm you computer. Here are some tips while cleaning your computer.
Clean your computer or mobile device once or twice a year.
Turn off and unplug your computer or mobile device before cleaning it.
Use compressed air to blow away dust.
Use an antistatic wipe to clean the exterior of the case and a cleaning solution and soft cloth to clean the screen.
Wednesday, 7 September 2016
Chapter 4 (a)
System Unit Components
September 7th, 2016. Wednesday.
Today we have learnt about the system unit components. The system unit itself is a case that contains electronic components of the computer used to process data. The inside of the system unit on a desktop personal computer includes drive bays, power supply, sound card, video card, processor, and memory. The motherboard is the main circuit board of the system unit. In other words, the motherboard is basically a computer chip that contains integrated circuits.
The processor, however, also called the central processing unit, interprets and carries out the basic instructions that operate a computer. A processor usually contains a control unit and an arithmetic logic unit. Type of processor may vary, such as a multi-core processor, dual-core processor, and a quad-core processor.
September 7th, 2016. Wednesday.
Today we have learnt about the system unit components. The system unit itself is a case that contains electronic components of the computer used to process data. The inside of the system unit on a desktop personal computer includes drive bays, power supply, sound card, video card, processor, and memory. The motherboard is the main circuit board of the system unit. In other words, the motherboard is basically a computer chip that contains integrated circuits.
The processor, however, also called the central processing unit, interprets and carries out the basic instructions that operate a computer. A processor usually contains a control unit and an arithmetic logic unit. Type of processor may vary, such as a multi-core processor, dual-core processor, and a quad-core processor.
- The control unit is the component of the processor that directs and coordinates most of the operations in the computer.
- The arithmetic logic unit performs arithmetic, comparison and other operations.
For every instruction, a processor repeats a set of four basic operations, which comprise a machine cycle. Four basic steps involves in a machine cycle includes fetch, decode, execute, and store. Most current personal computers support pipe-lining. This process begins fetching a second instruction before it completes the machine cycle for the first instruction.
The processor contains registers, that temporarily hold data and instructions. The system clock on the other hand controls the timing of all computer operations. The pace of the system clock is called the clock speed, and is measured in gigahertz.
A processor chip generates heat that could cause the chip to burn up. Therefore processors normally require some additional cooling technologies, such as heat sink, and liquid cooling technology.
Next, we have learnt about data representation. These include the understanding of analog signals and digital signals. Analog signals are continuous and vary in strength and quality. Whereas digital signals are in one of two states, which are on or off. Most computer we have today are digital.
The binary system uses two unique digits, which is 1 and 0 only. The American Standard Code for Information Interchange (ASCII) is the most widely used coding scheme to represent data.
Furthermore, we have studied about the memory. The memory consists of electronic components that store instructions waiting to be executed by the processor, data needed by those instructions, and the results of processing data. The memory also stores three basic categories of items, which are the operating system and other system software, application programs, data being processed, and the resulting information. Each location in memory has an address. Memory size is measured in kilobytes, megabytes, gigabytes, or even terabytes.
The system unit contains two types of memory, which is the volatile memory and the nonvolatile memory respectively. The volatile memory loses its contents when the power is turned off, example includes RAM. The nonvolatile memory does not lose its contents when the power is removed, example includes ROM, flash memory, and CMOS.
There are three basic types of RAM chips, which are:
- The amount of RAM necessary in a computer often depends on the types of software you plan to use.
Tuesday, 6 September 2016
Software for Systems
Chapter 3
September 6, 2016. Tuesday.
I did not blogged about yesterday because Ms.Wan had replaced the lecture class with a tutorial class instead. There is never much information to share about tutorial sessions, we received a quiz and submitted it within the given time period, that's basically it. Besides that, it has also made today's classes interestingly different as Ms.Wan have cancelled a tutorial session that we would normally have since we had already had it yesterday. But for today's class, Ms.Wan had talked about the whole of chapter 3, Software for Systems. It is an interesting chapter and I would brief more upon within this blog.
Application Software
For the very first topic of the day Ms.Wan had educated us about an Application Software. What is an application software? An application software consists of programs designed to make users more productive and/or assist with personal tasks. An application software comes in handy in many aspects in our daily basis. Such as to make business activities more efficient, to assist with graphics and multimedia projects, to support home, personal, and educational tasks, to facilitate communications, and many more. An application software comes in a variety of forms. These includes packaged software, custom software, web application, open source software, shareware, freeware, and public-domain software. System software serves as the interface between the user, the application software, and the computer's hardware respectively. In other terms, such are also known as utility programs.
Business Software
Next, we have moved on to business software. A business software is an application software that assists people while performing business activities.
Software for Home, Personal, and Educational Use
Application Software for Communications
September 6, 2016. Tuesday.
I did not blogged about yesterday because Ms.Wan had replaced the lecture class with a tutorial class instead. There is never much information to share about tutorial sessions, we received a quiz and submitted it within the given time period, that's basically it. Besides that, it has also made today's classes interestingly different as Ms.Wan have cancelled a tutorial session that we would normally have since we had already had it yesterday. But for today's class, Ms.Wan had talked about the whole of chapter 3, Software for Systems. It is an interesting chapter and I would brief more upon within this blog.
Application Software
For the very first topic of the day Ms.Wan had educated us about an Application Software. What is an application software? An application software consists of programs designed to make users more productive and/or assist with personal tasks. An application software comes in handy in many aspects in our daily basis. Such as to make business activities more efficient, to assist with graphics and multimedia projects, to support home, personal, and educational tasks, to facilitate communications, and many more. An application software comes in a variety of forms. These includes packaged software, custom software, web application, open source software, shareware, freeware, and public-domain software. System software serves as the interface between the user, the application software, and the computer's hardware respectively. In other terms, such are also known as utility programs.
Business Software
Next, we have moved on to business software. A business software is an application software that assists people while performing business activities.
- Word processing software allows users to create and manipulate documents. Such includes developing a document.
- Spreadsheet software allows users to organize data in rows and columns and perform calculations. Actions like charting depicts data in a spreadsheet in graphical form are part of a spreadsheet software.
- A database is a collection of data organized in a manner that allows access, retrieval, and use of that data. A database software allows users to create, access, and manage a database.
- Presentation software allows users to create visual aids for presentations to communicate ideas, messages, and other information to a group.
- Note taking software is a type of application software that enables user to enter typed text, handwritten comments, drawings, or sketches anywhere on a page.
- A software suite is a collection of individual programs available together as a unit.
- A personal information manager is an application software that includes appointment calendar, address book, notepad, etc.
- Scaled down versions of software are available to work with smart phones and other mobile devices.
- Project management software allows a user to plan, schedule, track, and analyze the events, resources, and cost of a project.
- Accounting software helps companies record and report their financial transactions.
- Document management software provides a means for sharing, distributing, and searching through documents by converting them into a format that can be viewed by any user.
- Enterprises typically require special computing solutions for various functional units.
Graphics and Multimedia Software
Software for Home, Personal, and Educational Use
- Personal finance software
- Legal Software
- Tax preparation software
- Personal DTP software
- Personal paint/image editing software
- Personal photo editing software\
- Clip art/image gallery
- Video and audio editing software
- Home design/landscaping software
- Travel and mapping software
- Reference software
- Educational software
- Entertainment software
Web Applications
A Web application is a Web site that allows users to access and interact with software from any computer or device that is connected to the Internet.
Application Software for Communications
- Web Browser
- Instant Messaging
- Chat Room
- Text, Picture, Video Messaging
- RSS Aggregator
- Blogging
- Newsgroup/Message Board
- FTP
- VoIP
- Video Conferencing
Learning Tolls for Application Software
Online Help is the electronic equivalent of a user manual. You can ask a question or access the Help topics in subject or alphabetical order. Web-based Help provides updates and more comprehensive resources to respond to technical issues about software.
A Web-based training is a type of CBT that uses Internet technology and consists of application software on the Web.
Distance learning is the delivery of education at one location while the learning takes place at other locations.
Wednesday, 31 August 2016
Chapter 2
Chapter 2 - Fundamentals of the World Wide Web and Internet
Independence day had just past yesterday and it is the beginning of a new month, September. Time flies, the year is already coming to an end. Today is a really special day, the 1st of September. It is our beloved lecturer Ms.Wan's birthday! Not to mention it is also my father's birthday today too, what a coincidence. The start of a new month, the start of a new chapter. Today Ms.Wan had started and as well as covered the whole of chapter 2 already, amazing.
Evolution of the Internet
What is the internet? The internet is a worldwide collection of networks that links millions of business, government agencies, educational institutions, and individuals. The internet is what make the world whole. It connects people from different places around the world. The internet originated as ARPANET in September 1969 and had only two main goals, which are :
- To allow scientist at different physical locations to share information and work together.
- To function if part of the network were disabled or destroyed by a disaster.
Years after ARPANET becomes functional, ARPANET has become known as the Internet in 1986. Internet is formed when NSF connects NSFnet to ARPANET. In 1995, NSFnet terminated it;s netword on the Internet and resumed status as a research network. Internet2 is then been founded in 1996. Today, more than 550 million hosts connects to the Internet. How astonishing, such a great achievement achieved by mankind.
Have you ever heard of an access provider? Well not me, I had no idea where this word had even originated from. But an access provider is a type of business that provides individuals and organizations access to the Internet free or for a fee, how intriguing. There are 3 types of service providers that we have learnt about today. Which are, ISP (Internet Service Provider), OSP (Online Service Provider, and WISP (Wireless Internet Service Provider).
- Regional ISP's provides internet access only to a specific geographical area, but national ISP's on the other hand provides internet access in cities and towns nationwide.
- As for OSP, it contains many members-only features. Popular OSP's include AOL (America Online) and MSN (Microsoft Network)
- Wireless Internet Service Providers provides wireless internet access to computers and mobile devices, although it may require a wireless modem in order to perform so.
The World Wide Web
The World Wide Web, or in others words just known as Web, consists of a worldwide collection of electronic documents (web pages). A Website is a collection of related Webpages and associated items. However, a Web server is a computer that delivers requested Webpages to your computer. Web 2.0 refers to Web sites that provide a means for users to interact.
Every Webpage has a unique address known as a URL or a Web address. A few terms of the internet or maybe tricks includes tabbed browsing. Tabbed browsing allows you to open and view multiple Web pages in a single Web browser window. This'll help you organize your work and will make multitasking much more easier.
Besides that, there are two different types of search tools which everyone that uses the Internet should be aware of, which are search engines and subject directories respectively. Search engines assists in finding information which are related to a specific topic whereas subject directories classifies Webpages in an organized set of categories. A search engine is helpful in locating items such as :
- Images
- Videos
- Audio
- Publications
- Maps
- People or Business
- Blogs
Did you know that some Web browsers contain an Instant Search box to eliminate the steps of displaying the search engine's Web page prior to entering the search text? These are some pretty interesting facts. There are up to thirteen types of Web sites, which includes :
Multimedia refers to any applications that combines text with :
- Graphics
- Animation
- Audio
- Video
- Virtual Reality
Graphics is a digital representation of a non-text information. It's formats include BMP, GIF, JPEG, PNG, and TIFF. For example, a thumbnail is a small version of a larger graphic.
Animation is the appearance of motion created by displaying a series of still images in sequence. Like a stop-motion, frame-by-frame kind of video.
Audio inlcudes music, speech, or any other sound. An audio file is normally able to be compressed such that it would take up lesser space.
Video consists of images displayed in motion.
Virtual reality is the use of computers to stimulate a real or imagined environment that appears as a three-dimensional space.
A plug-in is a program that extends the capability of Web browser. These also includes :
Web publishing is the development and maintenance of Webpages.
These developments go from planning a Website to Maintaining It.
Firstly as always you'll have to plan what type of website would you want to publish. Next you should analyze and design it such that it would attract users and operate accordingly. Once that's done you could move forward and begin creating and deploying the Website. Lastly, to ensure this Website lasts you'll need to maintain it regularly.
E-Commerce
E-commerce is a business transaction that occurs over an electronic network. E-commerce includes Business-to-Business, Business-to-Consumer, and Consumer-to-Consumer.
E-Retailing consists of 8 respective steps. Step 1, the customer displays the e-retailer's electronic storefront. Step 2, the customer collects purchases in an electronic shopping cart. Step 3, the customer enters payment information on a secure Website. The e-retailer the sends financial information to a bank. Step 4, the bank performs security checks and sends authorization back to the e-retailer. Step 5, the e-retailer's Web server sends confirmation to the customer, processes the order, and then sends it to the fulfillment center. Step 6, the fulfillment center packages the order, prepares it for shipment, and then sends a report to the server where records are updated. Step 7, while the order travels to the customer, shipping information is posted on the Web. And for the final step, step 8, the order will be delivered to the customer, who may be required to sign a handheld computer or document to acknowledge the receipt.
Other Internet Services
- E-mail is the transmission of messages and files via a computer network.
- An e-mail program allows you to create, send, receive, forward, store, print, and delete e-mail messages.
An e-mail message is traveled from a sender to a receiver through a couple of easy steps. Firstly it after it has been instructed to send, it will contact a software on your service provider's outgoing mail server. After that, the software on that particular server will determine the best route for the data and then sends the message. When the recipient finally checks the e-mail message, the message transfers from the incoming mail servers to the recipient's computer.
A mailing list is a group of e-mail names and address given a single name. For instance, subscribing adds your email name and address whereas unsubscribing removes it.
Instant messaging (IM) is a real- time Internet communications service. On the other hand, a chat is a real-time typed conversation that takes place on a computer. A chat room instead is a location on an Internet server that permits users to chat with each other.
VoIP (Voice over IP) enables users to speak to other users over the Internet. In other words also know as Internet Telephony.
A newsgroup is an online area in which users have written discussion about a particular subject. A message board is a Web-based type of discussion group.
Lastly we have FTP (File Transfer Protocol), FTP is an Internet standard that permits file uploading and downloading with other computers on the Internet. Surprisingly, many operating systems include FTP capabilities. Moreover, an FTP server is a computer that allows users to upload and/or download files using FTP.
Netiquette
Netiquette is the code of acceptable Internet behavior.
The lesson had eventually came to an end, we've covered so much in one day. I'm really surprised. Although all these might be a little hard to be absorbed in my brain for a day but I believe I would be able to get in down eventually. There is still so much to learn! I would not give up that easily.
And to Ms.Wan, if you are still reading this blog on the 1st of September, and hopefully you are, I wish you a happy and cheerful life ahead! Live every moment, today and always!! Happy Birthday!!
Subscribe to:
Comments (Atom)